User Behavior Analytics
Security Against Unknown Threats Through User Behavior
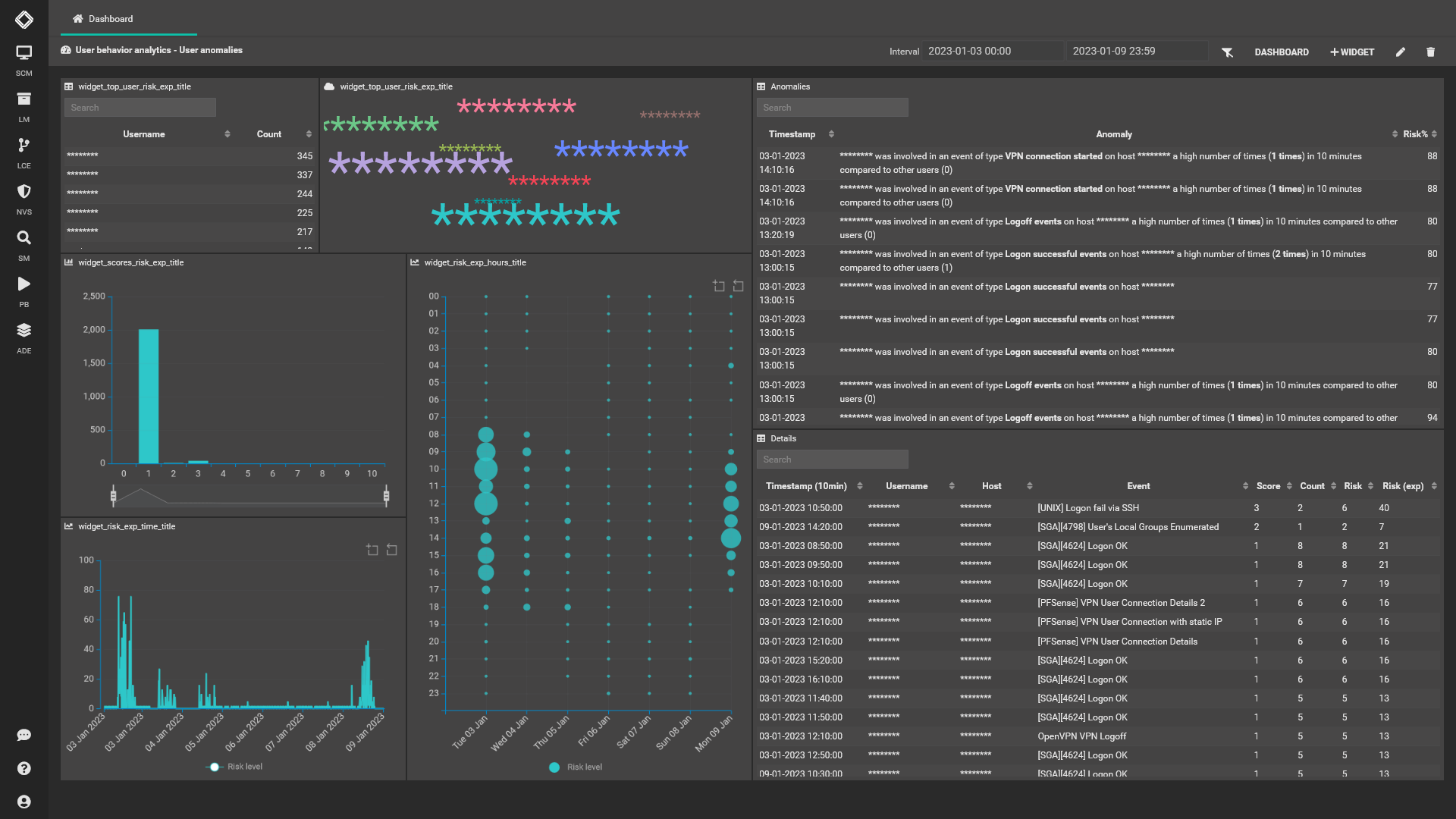
Our solution offers a User behavior analytics (UBA) application, able to detect insider threats and targeted attacks. Our UBA application is designed to define a baseline for each user and events related to the user, to create a reference and identify normal or anomalous behavior.


Monitor User Behavior to Discover Compromised Identities
The application learns about each user and creates a baseline of regular activities for each user and entity. Any activity that deviates from this baseline gets flagged as an anomaly. The UBA can identify user accounts taken over by attackers, because they exhibit anomalous behavior compared to the real business user.
Identify Privileged Account Abuse
UBA can help monitor accounts with administrative or escalated privileges, to ensure they are not being misused, either by their designated owner or by others. Privileged account issues include policy violations or neglectful acts which are not full blown attacks, but can have damaging results.
-

Accelerate Threat Hunting
Rapidly identify anomalous entities without human analysis. Receive notification when there is an unusual volume of events. -

User related risk
User behavior can be associated to risk categories not only on its volume. A set of dedicated widgets show, through trend indicators, the risk associated to users. -

Quick Implementation
No advanced configuration needed because the UBA automatically checks for all different situations starting from events.
-

Accelerate Threat Hunting
Rapidly identify anomalous entities without human analysis. Receive notification when there is an unusual volume of events. -

User related risk
User behavior can be associated to risk categories not only on its volume. A set of dedicated widgets show, through trend indicators, the risk associated to users. -

Quick Implementation
No advanced configuration needed because the UBA automatically checks for all different situations starting from events.

Benefits
- Collecting data about user activity
- Automatic reporting of abnormal behavior
- Risk category associated with user
- Alarms easy to understand
- Anomaly alerts showed directly in dashboards
Get A Free Evaluation Today
Contact us now to learn more.