Log Management
- MUCH MORE THAN A LOG REPOSITORY
Collection, Analysis and Advance Search
The Log Management module is able to manage log data and security-related events from any kind of data source with high performance of log ingestion and analysis. Adding IP sources the Log Management module automatically gathers and classify information to provide a clear overview of the security posture across the organization. The log is stored encrypted and signed to ensure data integrity and be compliant with major regulations. Due to an ultra-performing log ingestion engine, our Log Management module can collect a huge amount of security events from a lot of cyber security products (NIDS, firewall, AV, network devices, etc.), web application attacks and attempted information leaks that can be shown in a dynamic dashboard to facilitate investigation.
-
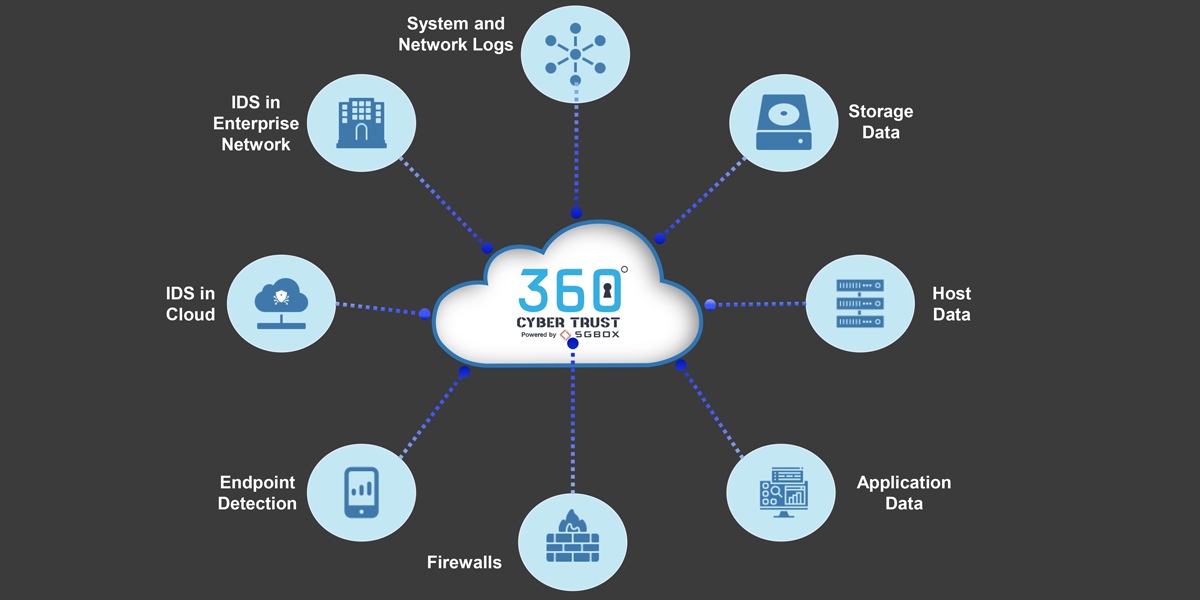
Collect LOG from any kind of data-source
Our Log Management module is able to collect any kind of log data format. In case of unknown log formats, such as custom application, is simple to generate the appropriate patterns to recognize all the security events. -
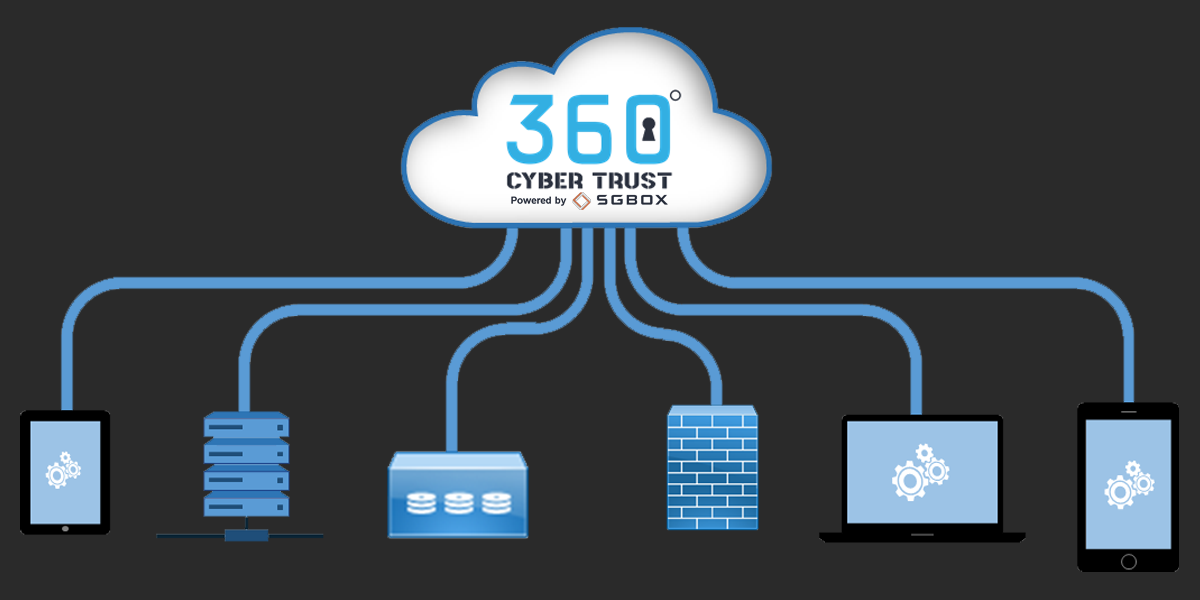
Agentless log collection
The Log Management module of our platform natively supports the standard Syslog, but was designed to gather logs of any format from any data source without the need for installing any proprietary agent specially designed for any specific platform. It has all been made possible by a powerful recognition engine and normalization of the logs which, through a simple, intuitive interface, allows the user to add freely logs from any of the company’s platforms. -

Analysis tool against anomaly scenarios
The function for detecting anomalies enables unusual situations concerning apparently consistent data traffic to be identified. Identification of anomalies is fundamental for the detection of frauds, network intrusions and other important events which would be impossible to identify. -
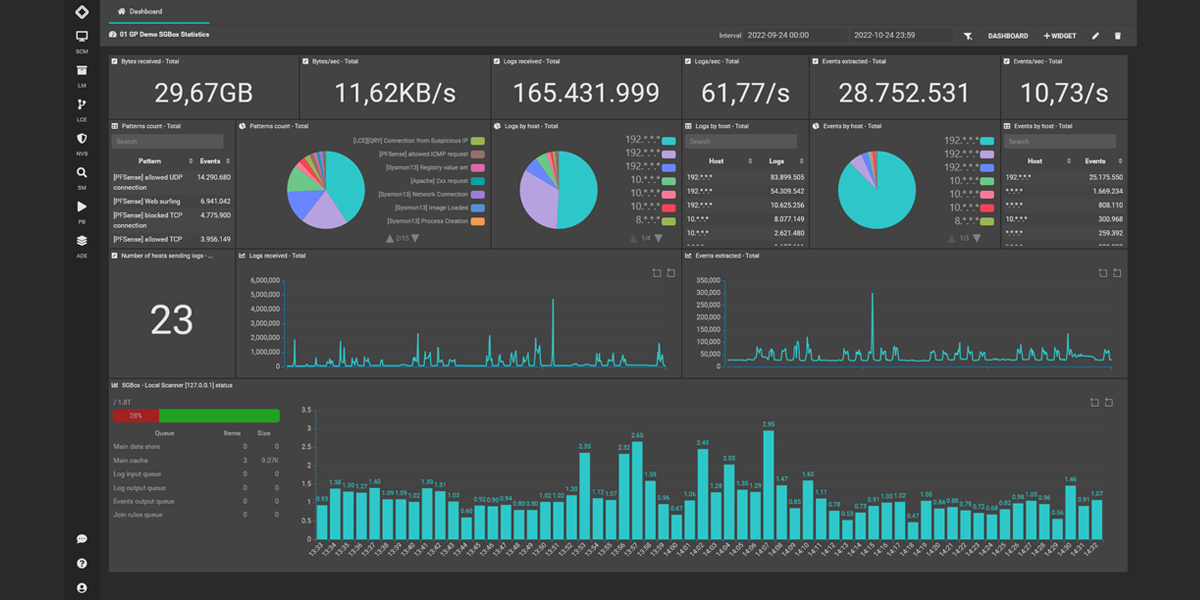
Custom graphs and reports
Using the flexibility of the user interface of the Log Management Module, it is possible to define a customized display of key information using a dashboard. Each user will be able to determine their own specific view of the most important elements of the information gathered, containing data of interest which relates to their own processes and operating area. -

Uncommon Simplicity
Powerfully designed and intuitive log aggregation, tagging, filtering, and searching for effective troubleshooting. Drill-down events, starting from an overview of historical data by entering in detail to analyze the single event.
-
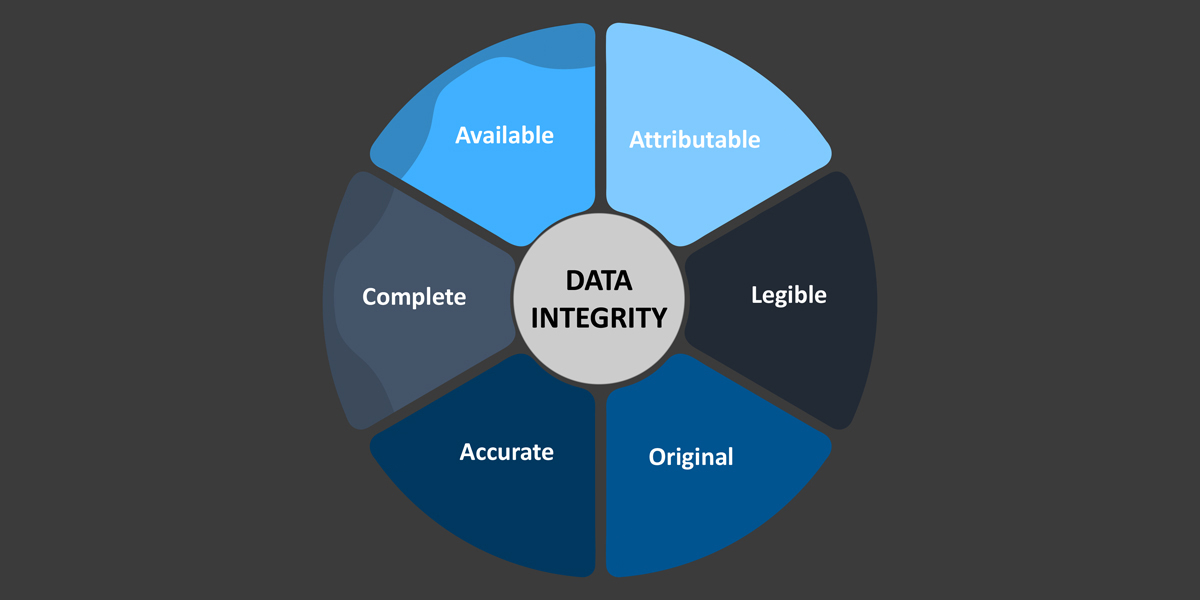
Data Integrity
Strong encryption with asymmetric keys are used to grant efficient log encryption of stored data. Timestamp and sign are used to certify the integrity of data. Unlimited data volume can be stored without time limitations.
-

Collect LOG from any kind of data-source
Our Log Management module is able to collect any kind of log data format. In case of unknown log formats, such as custom application, is simple to generate the appropriate patterns to recognize all the security events. -

Agentless log collection
The Log Management module of our platform natively supports the standard Syslog, but was designed to gather logs of any format from any data source without the need for installing any proprietary agent specially designed for any specific platform. It has all been made possible by a powerful recognition engine and normalization of the logs which, through a simple, intuitive interface, allows the user to add freely logs from any of the company’s platforms. -

Analysis tool against anomaly scenarios
The function for detecting anomalies enables unusual situations concerning apparently consistent data traffic to be identified. Identification of anomalies is fundamental for the detection of frauds, network intrusions and other important events which would be impossible to identify. -

Custom graphs and reports
Using the flexibility of the user interface of the Log Management Module, it is possible to define a customized display of key information using a dashboard. Each user will be able to determine their own specific view of the most important elements of the information gathered, containing data of interest which relates to their own processes and operating area. -

Uncommon Simplicity
Powerfully designed and intuitive log aggregation, tagging, filtering, and searching for effective troubleshooting. Drill-down events, starting from an overview of historical data by entering in detail to analyze the single event.
-

Data Integrity
Strong encryption with asymmetric keys are used to grant efficient log encryption of stored data. Timestamp and sign are used to certify the integrity of data. Unlimited data volume can be stored without time limitations.
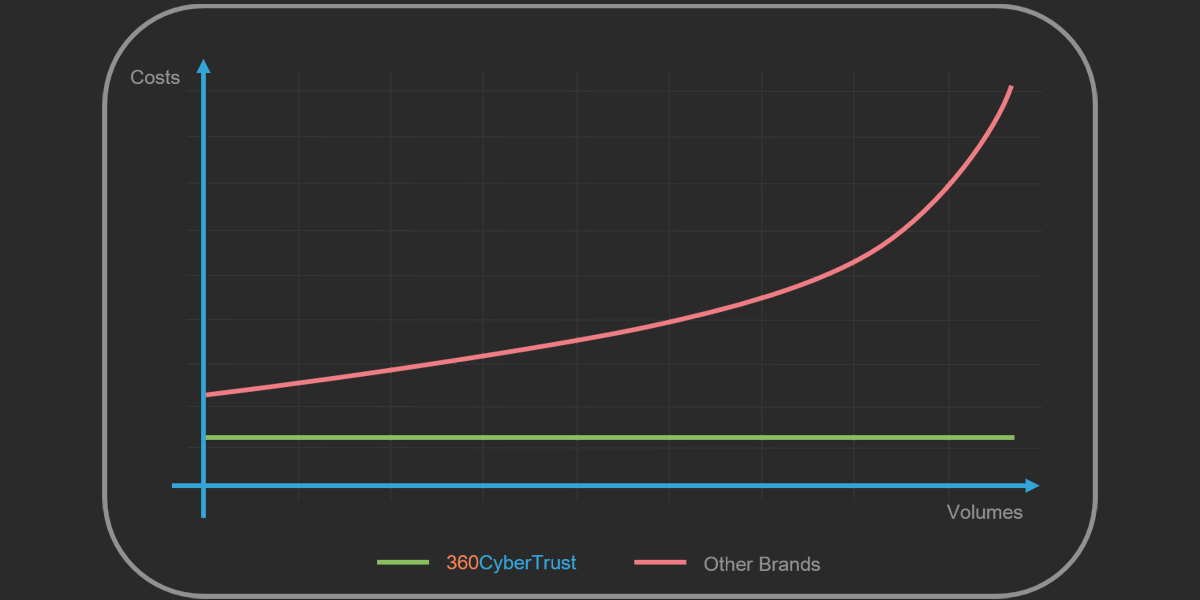
Easy Licensing
No need for complex volume calculation, our log management licensing is based on the number of devices generating log data, not on volume.

Compliance
Using our Log Management module, will help our customers in the process of compliance to main standards such as GDPR, ISO27001, SAMA, PCIDSS, etc. A set of out-of-the-box reports are ready to use
Get A Free Evaluation Today
Contact us now to learn more.

